Take note of the title of this blog. What you read below will give you some additional knowledge that may help you identify a hidden camera but it certainly won’t guarantee that.
We got lucky (if you can say that), the host had the hidden camera on the same network as the wifi that he allowed us access to and the stream was not protected (required authentication to access).
If a camera is hidden well and is not on the network (i.e. records to an internal memory card) or is on a network that you don’t have access to it may be very difficult to identify.
Below are the steps we are now taking when booking/staying at an Airbnb (or similar).
Step 1: Read the house listing in detail and view all photos
Before you book a house make sure you aren’t setting yourself up to fail.
- It is Airbnb policy that any cameras be detailed in the listing. Scroll through all the details as there doesn’t seem to be a defined place for the host to list these details. Details could be in the description, the amenities section, the safety features or the house rules.
- If a camera can be seen in a photo of the house listing then Airbnb deems that you have been notified of the cameras.
So, in summary if you want to avoid a house with cameras ensure that when you book it you have not been notified that there are cameras.
Step 2: Do a physical check of the house
- First, understand what you are looking for. Non-hidden cameras are pretty obvious and are readily identifiable as cameras. Hidden cameras unfortunately come in all shapes and sizes and are hidden in numerous objects.
Here are some examples:



.jpg)

A camera has to “see” to take an image so it needs a hole (although that can be as small as a pinhole) or a clear substrate to see through.
- Look for anything unusual in the rooms e.g. 2 smoke detectors in the same room, an alarm sensor but no alarm pad.
- A hidden camera will typically be placed so it has a field of view of what the person wants to see. So usually on a ceiling, bedside table, bathrooms, corners of rooms etc. Remember that these cameras typically have a wide field of view.
- Have a close look at any devices you find and see if you can see any lens. You can take photos using your phone up close with the flash or shine lights on them in the dark – the lens will usually reflect light.
Step 3: Scan the house network to identify potential cameras
Before we start you should note that a camera will not be discoverable on the network in the following circumstances:
- The camera is not on the same network as the network you have connected to. That is, if a host wants to hide a camera they can connect it to a network that you may not have access to.
- If the camera records to an internal memory card then it doesn’t need to be connected to a network and therefore wont show up on one.
- Connect to host accommodation network. Typically all host houses provide wireless access with a password. Once you are connected to the hosts wireless network you can then access the network to discover what is on it.
- Launch network scanning app and scan for devices connected to the network.
In my case I used an Android app called “Network Scanner – First Row”. There are many alternatives for Windows, Mac, iOS etc.

This app automatically scans the network you are connected to and displays the IP address of the device and the Manufacturer. See example output below.

As you can see the scan has identified a number of devices on the network including the Gateway (wireless access point / router), my laptop and several phones (Huawei and LG).
At this stage you should be looking for any giveaway signs that one of the devices is a camera. For example, the manufacturer could be IPCAMERA. (That was the case in the one I discovered 😂)
In this example the device at the bottom has raised my suspicions as it is not one of my devices (tick off your devices and see whats left) and the manufacturer is not a well known brand. For example we found it common to find the likes of Nest heating devices on the network.
I then use a port scanning app to see what ports (different options to connect to a device) are open on the device. This typically helps me identify the device.
I used the Android “Network Mapper” app.

Once you run the app you need to enter in the IP address of the device you want to port scan. In this case it is 192.168.0.116
The output of that port scan is below:
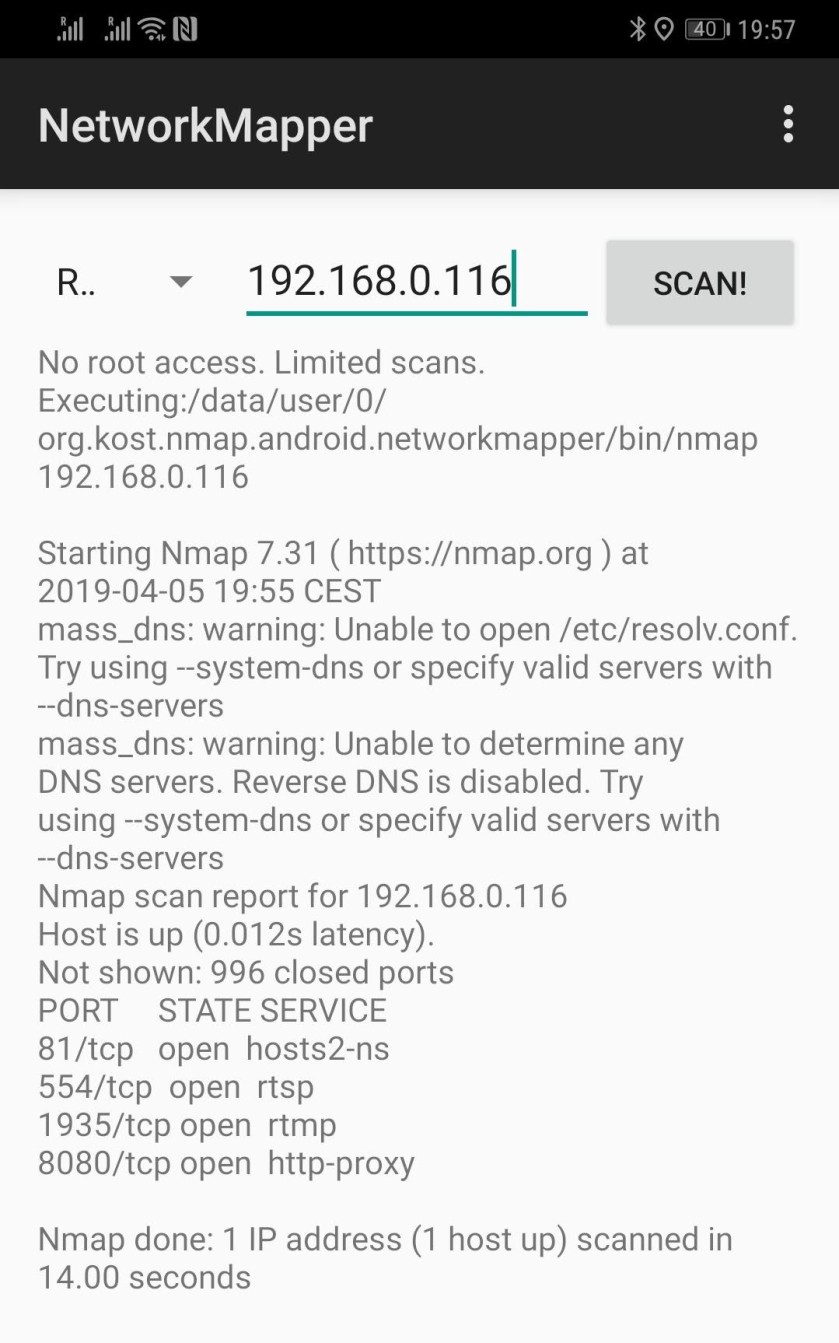
The details you are interested in are the Open ports detailed at the bottom of the scan.
In this example there are 4 ports open: 81, 554, 1935 and 8080 and the port scanner notes the typical service used on these ports.
You can Google the services and for this one you would discover that RTSP and RTMP services are used to stream video. Any ports that appear with the service HTTP or HTTPS can be attempted to be connected to with your web browser.
For example here is the output below when I connect to Port 8080 with my web browser:

The important thing to note from the output of the above is the mention of ONVIF. ONVIF is a standardised way of connecting to IP security cameras.
So, we can be fairly certain that this is a camera. In this instance this is a external camera that we were made aware of.
In our case finding and accessing the hidden camera was easy because:
- it was on the same nework as the wifi we were given access to
- it was named in the network scan as an “IPCAMERA”
- it had a live stream running on port 80 which could be connect to without requiring authentication (login and password)
In many cases accessing a hidden camera video stream may require more “invasive” techniques (e.g. password bruteforcing, vulnerability exploitation etc). Essentially hacking the devices to get access. Be aware that this may be illegal.
So, I hope that has provided some guidance. Just be careful sometimes a little knowledge can get you all paranoid without there actually being an issue.
