Russian military and intelligence operations are increasingly using GPS spoofing as a way to protect sensitive locations and cause disruption outside the country’s borders or in military zones, a report published this week has revealed.
The report, authored by the Center for Advanced Defense (C4ADS), analyzed 9,883 incidents of GPS spoofing incidents in and around Russia from the past three years.
C4ADS concluded that GPS spoofing attacks are emerging as a viable disruptive strategic threat and are now at high risk of proliferation among other belligerent nations, and the current 9,800+ incidents where Russia has deployed GPS spoofing equipment now stand as evidence to its effectiveness.
What is GPS spoofing?
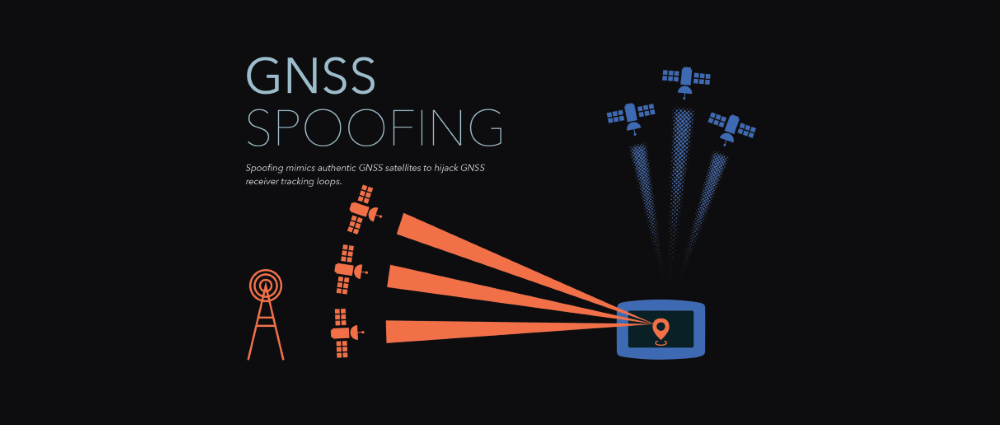
GPS spoofing refers to the practice of using fake GPS (Global Positioning) signals to trick equipment in the range of these false signals into relaying incorrect geo-location coordinates to GPS-capable devices.
The primary goal is to trick humans and devices into avoiding an area, or making GPS-based navigation unreliable in certain zones, also causing headaches for people, equipment, or operations in that specific area.
GPS spoofing should not be confused with GPS jamming, which is the practice of sending a strong radio signal that blocks “all” incoming GPS satellite signals from reaching GPS-capable devices in an area altogether, effectively shutting down GPS navigation, rather than making small modifications.

Image: C4ADS
GPS spoofing is also often referred to as GNSS spoofing, with GNSS standing for the Global Navigation Satellite System (GNSS), a term used to describe global positioning systems in general. The GPS system was developed and is still owned by the United States government. Other GPS-like systems also exist or are currently being developed, and are often described as GPS systems, although, a more accurate naming would be as GNSSes.
The practice of GPS spoofing isn’t new to any extent of the imagination. Scientists and military strategists have known all along that this is possible.
But while in previous decades GPS spoofing attacks required advanced knowledge to build and operate complex equipment that cost in the range of tens and hundreds of thousands of US dollars, this has changed in the past few years.
Thanks to the rise of cheap software-defined radios (SDRs) and publicly available and opensource GPS spoofing code, the cost of building GPS spoofers has gone down to as low as $300.
Russian GPS spoofing incidents
In a 66-page report released this week, C4ADS experts have listed the results of 9,883 instances of GPS spoofing that have been reported or reliably documented in areas in and around Russia.
C4ADS experts highlight that most of the incidents they’ve documented have been successful in confusing GPS-capable devices in the designated areas, showing that Russian forces are now regularly relying on this capability in war zones or contested geographical areas.
Most of the incidents have been reported around Ukraine and Crimea, where the Russian military is in an open conflict. Other incidents were also reported in Syria, where Russia has troops, but also around Russia’s border with NATO countries, and inside Russia itself, around sensitive government and intelligence buildings.
Image: C4ADS
The report lists some of the most high-profile GPS spoofing incidents that have taken place in the past three years. For example, C4ADS researchers make reference to several times when tens of ships passing through the Kerch Strait, which separates the Crimean Peninsula and the Russian mainland, reported seeing the GPS coordinates of the inland city of Tsibanobalka, rendering their satellite navigation systems useless in an area through which Russia often transports troops in and out of Crimea.
Image: C4ADS
They also documented incidents with ships approaching the Kerch Strait that received coordinates of an inland airport located in the city of Gelendzhik. It is believed this was done to confuse reconnaissance operations carried out in the area that rely on GPS-controlled drones.
Image: C4ADS
But while deploying GPS spoofing in Syria, Ukraine, and at its border with NATO states can be understood as a necessity to disrupt military reconnaissance and military operations, the same cannot be said for the use of the same technology inside Russia’s borders.
The report highlights that in many cases, GPS spoofing technology is also deployed above government buildings, military and intelligence locations, and above airports as a measure to prevent unauthorized drone-based surveillance, some of which may rely on GPS coordinates for their navigation systems.
Deploying GPS spoofing equipment ensures drones are tricked into steering away from sensitive locations that government officials don’t want surveilled.
Some of this is done for public safety, such as deploying the GPS spoofing equipment above airports, but in other cases similar equipment is often deployed at private residences to protect high-profile individuals, such as the country;s president, Vladimir Putin.
Conclusions
All in all, the report highlights the efficiency of such a basic and cheap attack, which is likely to spread to more countries, even to ones with limited military resources.
Besides military and intelligence uses, C4ADS experts also see GPS spoofing entering the private market as well.
“Russia continues to act as a pioneer in this space, exposing its willingness to not only deploy these capabilities in protection of VIPs and strategically-important facilities, but also to leverage these techniques to promote its ventures at frontiers in Syria and Russia;s European borders,” researchers said.
More details are available in C4ADS’ extensive “Above Us Only Stars” report, available for download as a PDF.